简介
从Kubernetes 1.8开始,Kubernetes通过Metrics API提供资源使用指标,例如容器CPU和内存使用率。这些度量可以由用户直接访问(例如,通过使用kubectl top命令),或者由集群中的控制器(例如,Horizontal Pod Autoscaler)使用来进行决策,具体的组件为Metrics-Server,用来替换之前的heapster,heapster从1.11开始逐渐被废弃。
Metrics Server是集群核心资源监控数据的聚合器,您可以在CCE控制台中快速安装本插件。
安装本插件后,可在“弹性伸缩”页面的“工作负载伸缩”页签下,创建HPA策略,具体请参见创建工作负载弹性伸缩(HPA)。
社区官方项目及文档:https://github.com/kubernetes-sigs/metrics-server。
作用
Metrics-Server的主要作用为为kube-scheduler,HorizontalPodAutoscaler等k8s核心组件,以及 kubectl top 命令和 Dashboard 等UI组件提供数据来源。
除此之外,也可以自定义Metrics-Server,添加一些其他的监控指标,比如说比较流行的 k8s-prometheus-adapter。
原理
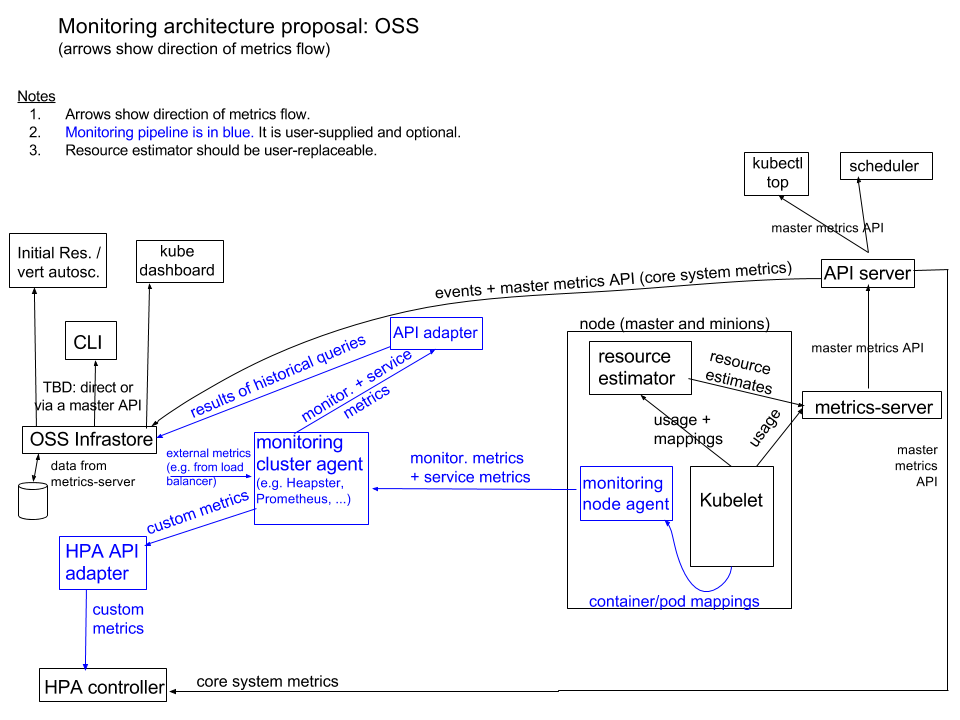
如何获取监控数据?
Metrics-Server通过kubelet获取监控数据。
在1.7版本之前,k8s在每个节点都安装了一个叫做cAdvisor的程序,负责获取节点和容器的CPU,内存等数据;而在1.7版本及之后,k8s将cAdvisor精简化内置于kubelet中,因此可直接从kubelet中获取数据。
原始数据过于分散且价值不高,因此需要一个叫做resource estimator的程序将来自kubelet的原始数据转换为估算值(如平均,求和)。该程序以DaemonSet方式运行,不过可能也内置于kubelet中。
如何提供监控数据?
Metrics-Server通过metrics API提供监控数据。
先说下API聚合机制,API聚合机制是k8s 1.7版本引入的特性,能将用户扩展的API注册至API Server上。
API Server在此之前只提供k8s资源对象的API,包括资源对象的增删查改功能。举例来说,yaml配置文件中的apiVersion字段描述的即是API名。
有了API聚合机制之后,用户可以发布自己的API,而Metrics-Server用到的metrics API和custom metrics API均属于API聚合机制的应用。
用户可通过配置APIService资源对象以使用API聚合机制,如下是metrics API的配置文件:
apiVersion: apiregistration.k8s.io/v1beta1
kind: APIService
metadata:
name: v1beta1.metrics.k8s.io
spec:
service:
name: metrics-server
namespace: kube-system
group: metrics.k8s.io
version: v1beta1
insecureSkipTLSVerify: true
groupPriorityMinimum: 100
versionPriority: 100
如上,APIService提供了一个名为v1beta1.metrics.k8s.io的API,并绑定至一个名为metrics-server的Service资源对象。
可以通过kubectl get apiservices命令查询集群中的APIService。
因此,访问Metrics-Server的方式如下:
/apis/metrics.k8s.io/v1beta1 ---> metrics-server.kube-system.svc ---> x.x.x.x
+---------+ +-----------+ +------------------------+ +-----------------------------+
| 发起请求 +----->+ API Server +----------------->+ Service:metrics-server +-------->+ Pod:metrics-server-xxx-xxx |
+---------+ +-----------+ +------------------------+ +-----------------------------+
有了访问Metrics-Server的方式,HPA,kubectl top等对象就可以正常工作了。
安装插件
wget https://github.com/kubernetes-sigs/metrics-server/releases/latest/download/components.yaml
修改配置:
apiVersion: v1
kind: ServiceAccount
metadata:
labels:
k8s-app: metrics-server
name: metrics-server
namespace: kube-system
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
labels:
k8s-app: metrics-server
rbac.authorization.k8s.io/aggregate-to-admin: "true"
rbac.authorization.k8s.io/aggregate-to-edit: "true"
rbac.authorization.k8s.io/aggregate-to-view: "true"
name: system:aggregated-metrics-reader
rules:
- apiGroups:
- metrics.k8s.io
resources:
- pods
- nodes
verbs:
- get
- list
- watch
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
labels:
k8s-app: metrics-server
name: system:metrics-server
rules:
- apiGroups:
- ""
resources:
- pods
- nodes
- nodes/stats
- namespaces
- configmaps
verbs:
- get
- list
- watch
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
labels:
k8s-app: metrics-server
name: metrics-server-auth-reader
namespace: kube-system
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: extension-apiserver-authentication-reader
subjects:
- kind: ServiceAccount
name: metrics-server
namespace: kube-system
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
labels:
k8s-app: metrics-server
name: metrics-server:system:auth-delegator
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: system:auth-delegator
subjects:
- kind: ServiceAccount
name: metrics-server
namespace: kube-system
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
labels:
k8s-app: metrics-server
name: system:metrics-server
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: system:metrics-server
subjects:
- kind: ServiceAccount
name: metrics-server
namespace: kube-system
---
apiVersion: v1
kind: Service
metadata:
labels:
k8s-app: metrics-server
name: metrics-server
namespace: kube-system
spec:
ports:
- name: https
port: 443
protocol: TCP
targetPort: https
selector:
k8s-app: metrics-server
---
apiVersion: apps/v1
kind: Deployment
metadata:
labels:
k8s-app: metrics-server
name: metrics-server
namespace: kube-system
spec:
selector:
matchLabels:
k8s-app: metrics-server
strategy:
rollingUpdate:
maxUnavailable: 0
template:
metadata:
labels:
k8s-app: metrics-server
spec:
containers:
- args:
- --kubelet-insecure-tls # 取消证书验证,避免 X509 报错
- --cert-dir=/tmp
- --secure-port=443
- --kubelet-preferred-address-types=InternalIP,ExternalIP,Hostname
- --kubelet-use-node-status-port
- --metric-resolution=15s
image: k8s.gcr.io/metrics-server/metrics-server:v0.5.0
imagePullPolicy: IfNotPresent
livenessProbe:
failureThreshold: 3
httpGet:
path: /livez
port: https
scheme: HTTPS
periodSeconds: 10
name: metrics-server
ports:
- containerPort: 443
name: https
protocol: TCP
readinessProbe:
failureThreshold: 3
httpGet:
path: /readyz
port: https
scheme: HTTPS
initialDelaySeconds: 20
periodSeconds: 10
resources:
requests:
cpu: 100m
memory: 200Mi
securityContext:
readOnlyRootFilesystem: true
runAsNonRoot: true
runAsUser: 1000
volumeMounts:
- mountPath: /tmp
name: tmp-dir
nodeSelector:
kubernetes.io/os: linux
priorityClassName: system-cluster-critical
serviceAccountName: metrics-server
volumes:
- emptyDir: {}
name: tmp-dir
---
apiVersion: apiregistration.k8s.io/v1
kind: APIService
metadata:
labels:
k8s-app: metrics-server
name: v1beta1.metrics.k8s.io
spec:
group: metrics.k8s.io
groupPriorityMinimum: 100
insecureSkipTLSVerify: true
service:
name: metrics-server
namespace: kube-system
version: v1beta1
versionPriority: 100
kubectl apply -f components.yaml
配置
--kubelet-preferred-address-types - The priority of node address types used when determining an address for connecting to a particular node (default [Hostname,InternalDNS,InternalIP,ExternalDNS,ExternalIP])
--kubelet-insecure-tls - Do not verify the CA of serving certificates presented by Kubelets. For testing purposes only.
--requestheader-client-ca-file - Specify a root certificate bundle for verifying client certificates on incoming requests.
Kubectl top
node
kubectl top node
NAME CPU(cores) CPU% MEMORY(bytes) MEMORY%
server1 266m 6% 6342Mi 82%
worker1 60m 3% 1595Mi 43%
worker2 75m 3% 1224Mi 33%
pod
kubectl top pod
NAME CPU(cores) MEMORY(bytes)
csi-rbd-demo-pod 1m 2Mi
csi-rbdplugin-p7bwg 1m 62Mi
csi-rbdplugin-provisioner-7574fbcd7d-pwlr6 5m 224Mi
csi-rbdplugin-twjbm 1m 122Mi
注意
Metrics Server基于 内存 存储, 重启后数据将全部丢失,而且它仅能留存最近收集到的指标数据,因此,如果用户期望访问历史数据,就不得不借助于第三方 的监控系统( 如 Prometheus 等)。
